Concentric provides agentless connectivity to a wide variety of data repositories so you can govern access to your data wherever it resides. We process both structured and unstructured data in the cloud or on-premises. We also integrate with popular data classification frameworks, like Microsoft Information Protection, so you can enjoy better coverage and more accurate classification results throughout your security stack. If you don’t see what you need on our list, let us know. Our professional services team will make quick work of getting your data connected.
Click below to see our complete list of available integrations.

The Semantic Intelligence solution finds and catalogs file content, metadata, usage patterns, location, regulated data, and security context to give you a crystal-clear picture of a file’s sensitivity and role within your organization. Unlike other solutions that use rules or regular expressions, Concentric’s deep learning engine works autonomously, accurately, and without end-user involvement.
With over 240 categories out of the box (and available customization for your specialized use cases), we categorize everything from source code to contracts to PII/PHI/PCI and more – no matter where your data is located or which folder it’s in. Now you can focus on data content instead of data location.

Your users are content experts, and the way they share, use, and store files reveals critical information about appropriate access, data use, and risk. Risk Distance analysis compares the security context of each individual file with its peers to identify risk and oversharing. Concentric’s deep learning engine autonomously taps into user content expertise without requiring rules, regex, or document tagging performed by end users.
Once your files are categorized and assessed for risk, you’re ready for data access governance at scale. Concentric offers a range of tools that can update critical security and access parameters from a single, centralized location. Adding or correcting classification tags on a group of files, for example, is a common data access governance task that can be completed with just a few keystrokes. And if you already use a document classification system (such as Microsoft’s MIP framework), we integrate with your existing tags. Updating access permission, fixing entitlements, changing access control rules, limiting sharing options, moving data to the right location or deleting data are other remediation activities you can easily complete with Concentric.
Your users are content experts, and the way they share, use, and store files reveals critical information about appropriate access, data use, and risk. Risk Distance analysis compares the security context of each individual file with its peers to identify risk and oversharing. Concentric’s deep learning engine autonomously taps into user content expertise without requiring rules, regex, or document tagging performed by end users.
MIND deep-learning-as-a-service selects the best AI model for your organization.
Peer-file analysis continually protects data without overhead or end-user involvement.

Find business-critical data, files stored in the wrong location, and oversharing by users. Gain essential insights into risk and mitigation opportunities.
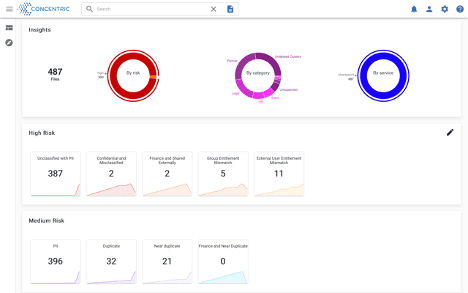



Watch how a high tech customer protects from insider risk using Concentric Semantic Intelligence

See how Semantic Intelligence can discover data and classify content without rules or regex

Libero nibh at ultrices torquent litora dictum porta info [email protected]
Start connecting your payment with Switch App.