Autonomous, Content-Centric Email and Messaging Data Security
Top 5 Cloud Messaging and Email
Security Challenges
• Comprehensive protection
• You can't protect what you can't see
• Balance security and user experience
• Compliance and data risk mitigation
• Autonomous operation

Worried about data flowing through communication channels?
“Email, Slack, and Teams are double-edged swords. They’re unmatched as productivity tools, but they also create huge potential for data loss. Malicious actions or simple human error can easily expose business-critical data to unauthorized users
Do you need to find and protect sensitive data across Email, Slack and Teams?
Discovery is key
What separates a good data security strategy from a great one? Knowing what’s business-critical (and what’s not) makes all the difference.
Our deep learning engine scans your data to identify and protect critical content. We categorize everything from source code to contracts to PII/PHI/PCI and more – across text and attachments.
Want to know how it works?
Protect your data without burdening your end users
Is data protection and usability a zero-sum game? Your users want total freedom to collaborate. Your security approach has to keep up.
Relying on rules to self enforce data security isn’t working. Cumbersome rule writing and management overhead introduce tons of false positives, don’t provide the coverage needed and have ensured underwhelming data protection. With Semantic Intelligence™, you’ll automate data security without rules, policies, or end-user involvement.
Wondering how it works in the real world?
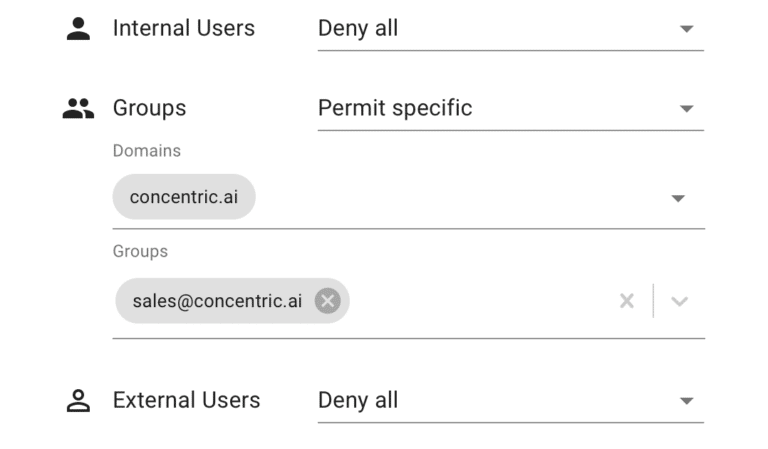
Risk Reduction is the Goal
No security solution is an island. Policy enforcement, regulatory compliance, and risk monitoring all depend on reliable, up-to-date risk information.
Concentric consolidates risk insights with a content-centric UI that makes remediation a breeze. Update critical security and access parameters from a single, centralized location, or integrate with your existing security architecture. It’s that easy.
How will it work for you?
Scale your data protection without having to scale your security teams
Security staff in short supply? You’re not alone. Cloud data security automation is the answer.
Our Risk Distance™ analysis technology takes labor and guesswork out of the equation. By comparing security practices of sensitive data to similar data, we can give you autonomous security insights such as inappropriate sharing, data leakage without an army of security analysts.
Want to see how it works?
Powerful AI Technologies
Simplify and Automate Cloud Data Security
Content-Focused Data Discovery
Our deep learning engine autonomously discovers sensitive cloud content
- Powerful natural language processing technology for accuracy and efficiency
- Over 250 business-relevant data categories
- Easily find regulated and sensitive content across email and messaging tools
Continuous Risk Monitoring and Protection
Stay vigilant to prevent cloud data loss and reduce risk exposure
- Prevent oversharing via email or workspace channels
- Spot data inappropriately shared with third parties
- Disable access, recall messages and integrate with SOC and end user notification workflows
Simple, Low Overhead
Reduce IT investments and end-user content consultations
- No rules or regex required
- No cumbersome risk policy definition
- SaaS deployment
Let's Get Started!
Get Concentric's free risk security assessment report for messaging and email communications
Find business-critical data, text and attachments being shared inappropriately with employees, groups or third parties. Gain visibility and establish control over your .
- Designed for dispersed, multi-channel messaging environments
- Develop and implement a plan for least-privileges based access control
- Find and protect sensitive text/attachments from ending up in the wrong hands
Demos
Learn About Semantic Intelligence™

Learn how Concentric Semantic Intelligence is protecting PHI data for a healthcare firm


See how Semantic Intelligence can discover data and govern access to content without rules or regex